Transitioning an entire internet ecosystem away from legacy protocols like Transport Layer Security TLS 1.0 and 1.1 is more complex. Countless systems rely on these outdated standards, creating major technical hurdles. This article will explore why upgrading to TLS 1.2 and 1.3 has taken so long and what this means for organisations.
Timeline of the TLS Protocols
Let's quickly review the protocol's history and subsequent versions:
- TLS 1.0 (1999): Introduced to replace SSL 2.0 and SSL 3.0. It was published under RFC 2246 and later deprecated in March 2021 (RFC 8996).
- TLS 1.1 (2006): A minor update to TLS 1.0 under RFC 4346. It improved on some weaknesses but failed to gain widespread use and was also deprecated under RFC 8996.
- TLS 1.2 (2008): This version (RFC 5246) remains today's most commonly used protocol. Though technically succeeded by TLS 1.3, it still dominates internet traffic.
- TLS 1.3 (2018) : A more modern and secure protocol, published as RFC 8446. Adoption continues to grow, though it trails behind TLS 1.2.
The timeline of these protocols reflects the slow, steady migration away from outdated encryption standards to safer alternatives.
How Many Websites Still Support TLS 1.0 and 1.1?
As of May 2024, a significant number of websites still allow these outdated protocols. Qualys SSL Labs reports:
- 27.9% of websites still support TLS 1.0.
- 30% still support TLS 1.1.
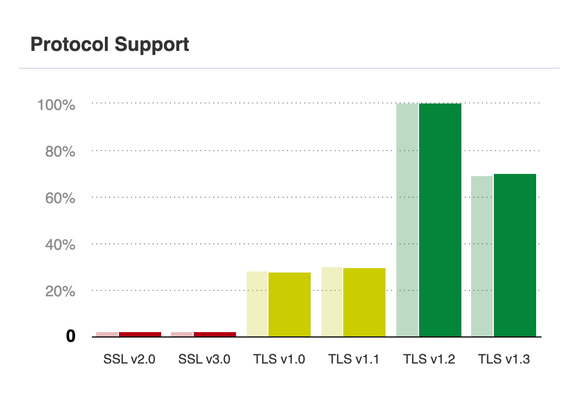
In contrast, 99.9% of websites support TLS 1.2, and 70.1% have adopted TLS 1.3. While the adoption of TLS 1.3 is improving, some websites rely on older protocols due to legacy systems.
Why Is Migrating from TLS 1.0 and 1.1 Essential?
The primary reason for abandoning TLS 1.0 and 1.1 is security. These protocols are decades old, and their encryption capabilities must be improved to protect against modern cyber threats.
- Outdated Cryptography: TLS 1.0, launched over 25 years ago, uses weak cipher suites that are vulnerable to attack. TLS 1.1 offered minor improvements but still shared similar flaws.
- Incompatibility with Quantum-Resistant Algorithms: Post-quantum cryptography (PQC) — a critical future security measure — isn't compatible with earlier TLS protocols. Implementations of TLS 1.3 already support some PQC algorithms, but TLS 1.2 and older protocols cannot be retrofitted.
- Regulatory Standards and Industry Compliance: Organisations must comply with frameworks like PCI DSS and NIST, which require dropping support for outdated protocols. These standards emphasise the need for TLS 1.2 and TLS 1.3 to protect sensitive data.
What Makes the Transition So Difficult?
Migrating to newer protocols like TLS 1.2 and 1.3 is more complex than flicking a switch. The process requires updating countless components across systems, including:
- Web server software and hosting tools (e.g., cPanel).
- Devices and hardware reliant on legacy protocols.
- Content delivery networks (CDNs).
- Internal networks, IoT devices, and payment systems.
Additionally, software libraries (like OpenSSL) and platforms such as Microsoft Azure must support these transitions. Often, upgrades can only proceed once dependencies are resolved across interconnected systems.
The Path for Transitioning Away from TLS 1.0 and 1.1
To transition from TLS 1.0 and 1.1, organisations must eliminate dependencies on these outdated protocols to avoid compliance issues and security risks. This involves developing a migration plan to outline the necessary steps for upgrading systems, servers, and endpoints; auditing systems using tools to identify outdated protocol usage; updating software, including web clients, frameworks, and servers, to support TLS 1.2 or higher; testing applications for any hard-coded legacy protocol dependencies; and effectively communicating these changes to stakeholders, partners, and users to minimise potential disruptions.
Final Thoughts
The retirement of TLS 1.0 and 1.1 marks a significant step toward a safer internet. While the migration has been slow, it's a crucial measure to protect against evolving cyber threats. Organisations must prioritise upgrading to TLS 1.2 or, ideally, TLS 1.3 to ensure data security and compliance.
With lessons learned from this transition, the industry is better prepared for even bigger changes, such as implementing post-quantum cryptography. Staying ahead of the curve is essential to safeguard the future of internet security.
Discussions and Comments
Click here to view and join in on any discussions and comments on this article.

